For the first time today, I ran into a django website that was in production and had DEBUG=True in the settings file.
This was https://patients.amdc.com.mv/paymentstatus/ and an error was thrown on this url.
How I found this url is also because of DEBUG=True, as all 404 error pages would display all the endpoints of the site.
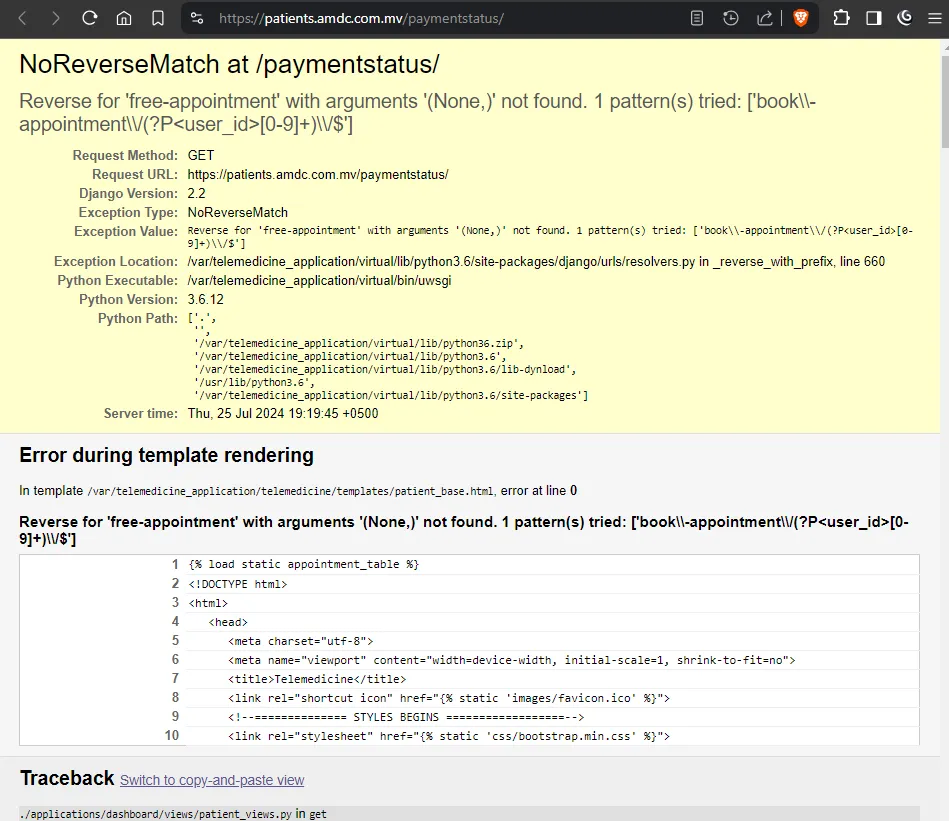
I had run into many such Laravel sites in the past, (Red.mv, avas.mv and more) and all of them had atleast one secret exposed in the error page.
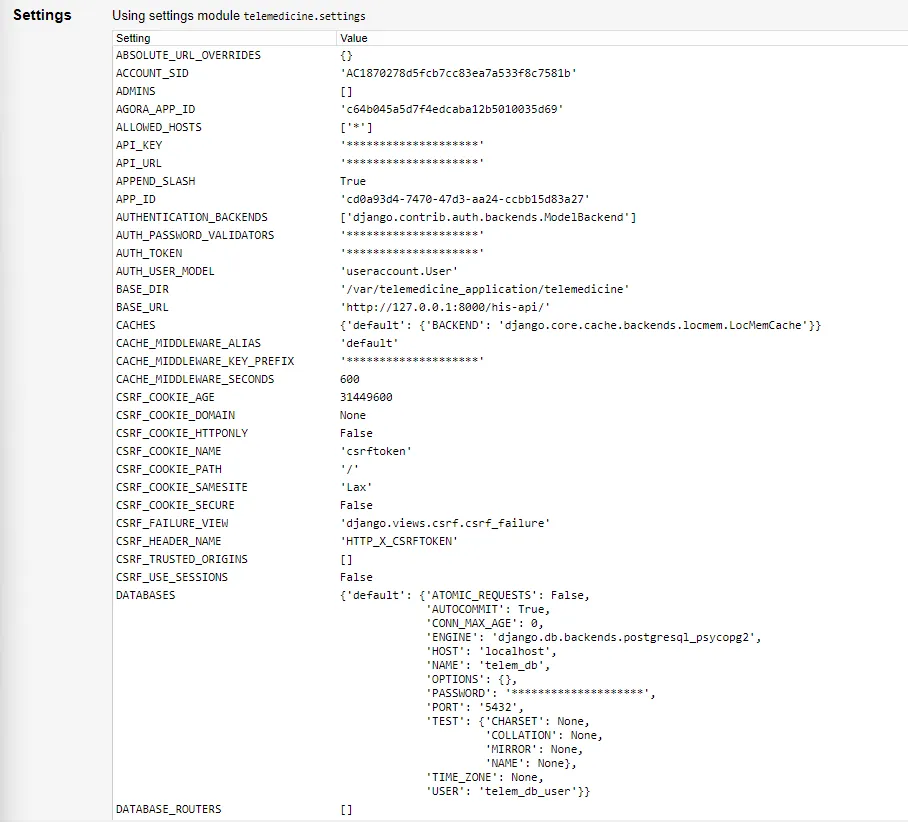
However, this error page from django had the secrets filtered out. I dug a little and found out that Django has a
built-in mechanism to filter out sensitive information from error pages using a SafeExceptionReporterFilter.
Had me wondering how other frameworks tackle this and if they do. (Obviously, the best way is to never have DEBUG=True
in production)
Sensitive data filtering in Django
As mentioned, Django provides a built-in mechanism to protect sensitive information from being exposed. Even when debug
mode is enabled (DEBUG=True), Django hides sensitive data from error messages through SafeExceptionReporterFilter.
This class filters out sensitive information from error reports using a regular expression that identifies sensitive
patterns, such as API keys and secrets.
class SafeExceptionReporterFilter: """ Use annotations made by the sensitive_post_parameters and sensitive_variables decorators to filter out sensitive information. """
cleansed_substitute = "********************" hidden_settings = _lazy_re_compile( "API|TOKEN|KEY|SECRET|PASS|SIGNATURE|HTTP_COOKIE", flags=re.I )
def cleanse_setting(self, key, value): ...Laravel wants developers to be careful
A user from the Laravel community raised a similar concern about sensitive information being exposed in error messages
when debug mode is enabled (issue #26750). However this issue was
ignored due to the attitude the OP had towards the issue. The Laravel community believes that developers should be
careful with setting APP_ENV. But I still think the OP had a point
when he said
“YOU DON’T PRINT PASSWORDS ON A FREAKING HTML PAGE”.
Laravel provides options for encrypting environment variables which is the main aproach rails takes.
Rails has encrypted environment variables
Ruby on Rails takes a different yet better approach by encrypting environment variables through a master key. Rails
provides a built-in mechanism called encrypted secrets to store sensitive information securely. This feature allows
developers to encrypt secrets and store them in a config/credentials.yml.enc file. The master key is used to decrypt
these secrets at runtime.
For Django users seeking similar functionality, a third-party package called django-encrypted-secrets provides the same behavior as Rails encrypted secrets.